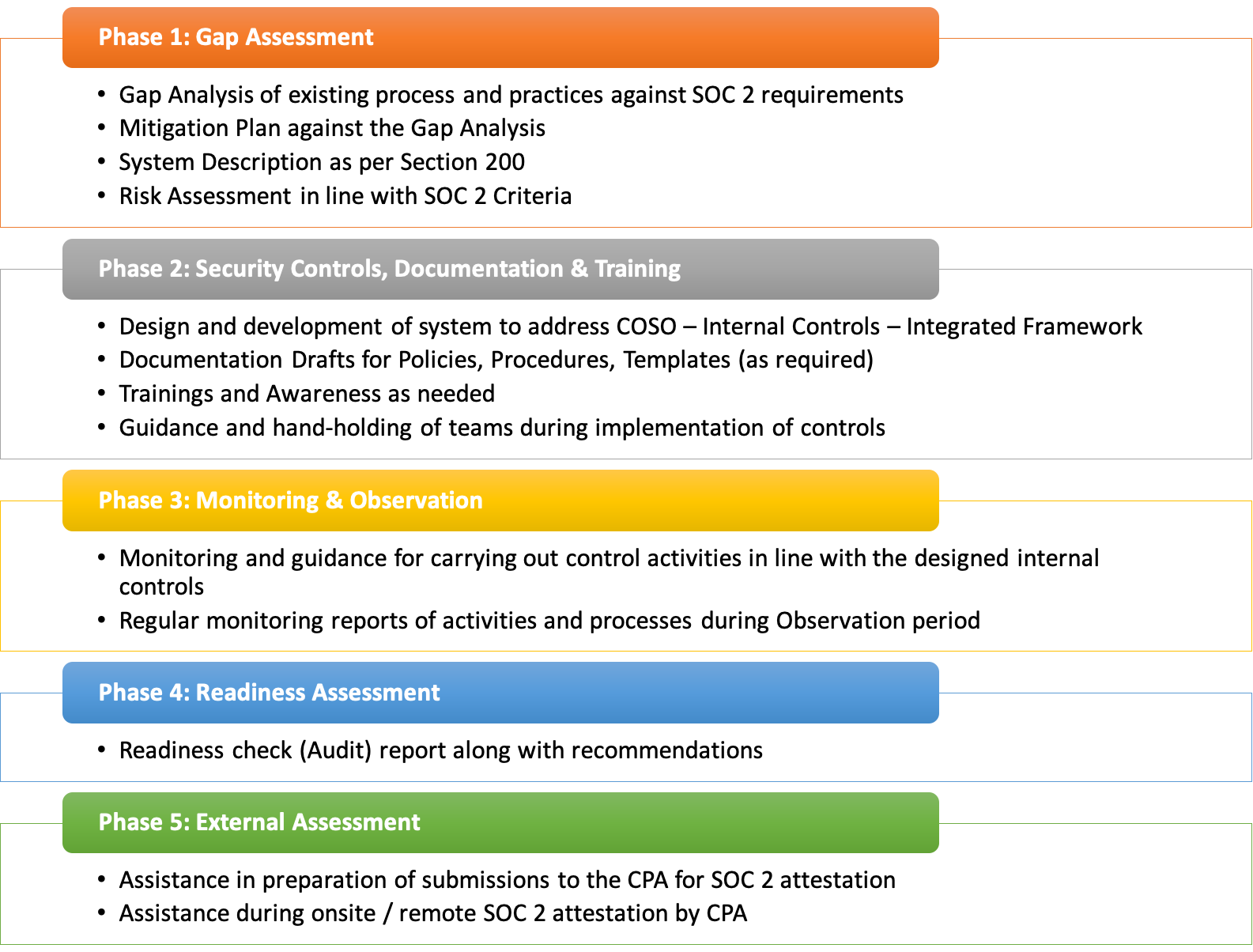
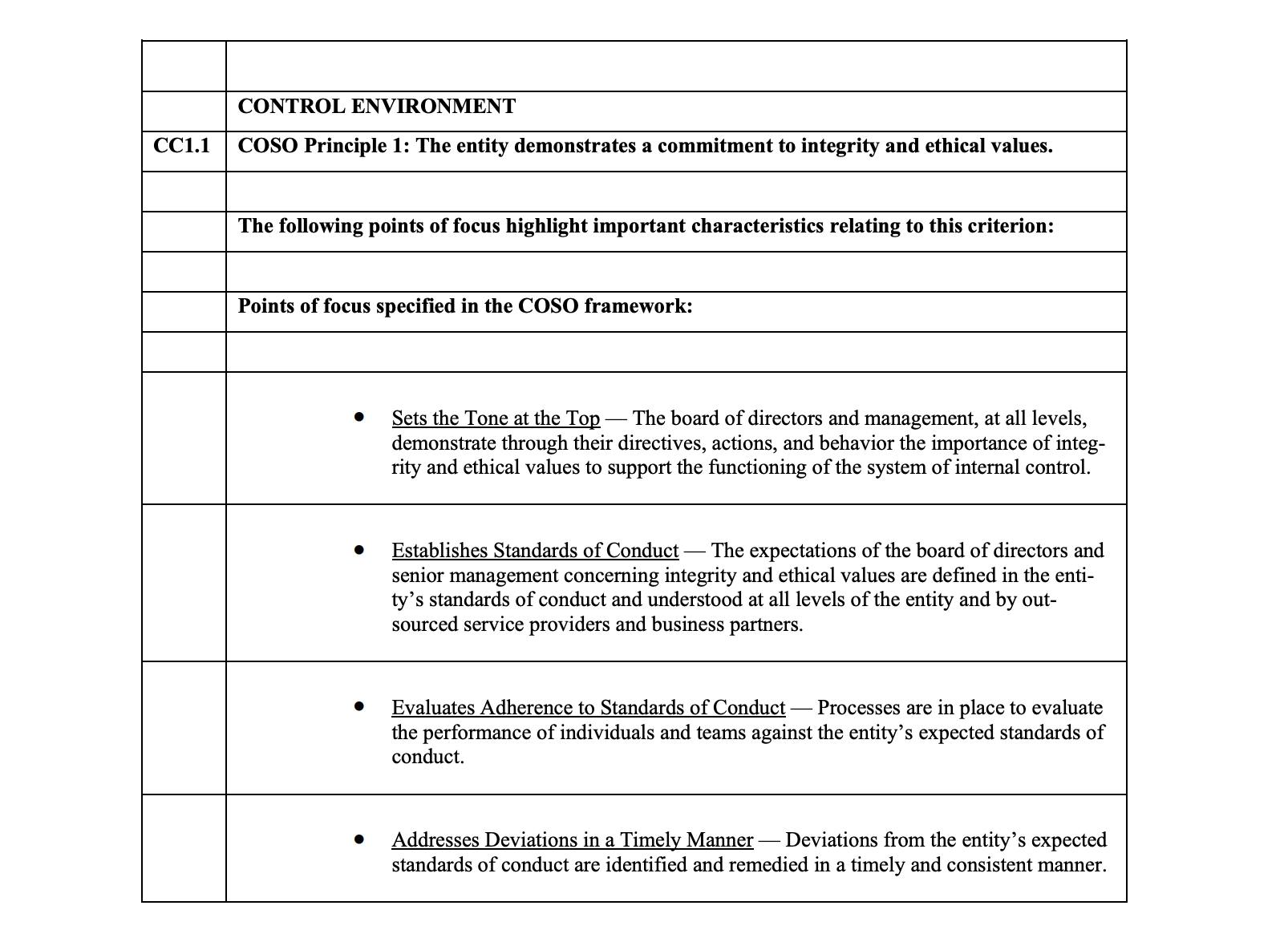
Soc 2 Policy Templates
Soc 2 Policy Templates - Learn what a soc 2 policy template is and why you need them for your compliance project. We have dedicated support ready to. Preparing for a soc 2 audit requires a thorough annual review of your security documentation and processes. These policies are reviewed by the soc 2 auditor in great detail with respect to adherence to soc 2 controls and are expected to be documented and accepted by each. Establish zero trust policies that align with soc 2 trust service criteria. Policies must cover key areas like data protection, access controls, incident response, and employee responsibilities. Browse our library of ebooks, policy templates, audit readiness checklists, evidence spreadsheets, and more free tools to simplify and streamline compliance. The objective is to account for: Save hundreds of hours and thousands of dollars on annual soc 2 compliance costs. Our goal is to create quality templates so that our customers can avoid rework and focus on their actual jobs rather than doing everything from scratch. Track version history and changes to ensure continued. Our goal is to create quality templates so that our customers can avoid rework and focus on their actual jobs rather than doing everything from scratch. Comply is free soc 2 compliance software for soc 2 certification. Establish zero trust policies that align with soc 2 trust service criteria. Define roles and responsibilities for implementing and maintaining these policies. By providing businesses with a structured framework, soc 2 templates can save significant resources and time within the policy development stage. To avoid the loss of opportunities that could positively affect your business, getting a better understanding of how to influence your soc 2 report and how to use soc 2 policy. Review security policies and procedures. Edit and customize the policy to your organization’s needs; The objective is to account for: Review security policies and procedures. These policies are reviewed by the soc 2 auditor in great detail with respect to adherence to soc 2 controls and are expected to be documented and accepted by each. The system and organization controls (soc) 2 report, developed by the american institute of cpas (aicpa), has become a crucial standard for evaluating and demonstrating. Soc 2 policies are a comprehensive set of guidelines and procedures that a company’s it department follows to handle and protect customer data. An access control policy defines how your organization manages user access to systems, data, and applications. Comply is free soc 2 compliance software for soc 2 certification. Preparing for a soc 2 audit requires a thorough annual. To avoid the loss of opportunities that could positively affect your business, getting a better understanding of how to influence your soc 2 report and how to use soc 2 policy. Establish zero trust policies that align with soc 2 trust service criteria. The system and organization controls (soc) 2 report, developed by the american institute of cpas (aicpa), has. Preparing for a soc 2 audit requires a thorough annual review of your security documentation and processes. Establish zero trust policies that align with soc 2 trust service criteria. These policies are reviewed by the soc 2 auditor in great detail with respect to adherence to soc 2 controls and are expected to be documented and accepted by each. An. Comply is free soc 2 compliance software for soc 2 certification. Learn what a soc 2 policy template is and why you need them for your compliance project. These policies are reviewed by the soc 2 auditor in great detail with respect to adherence to soc 2 controls and are expected to be documented and accepted by each. The system. Review security policies and procedures. To avoid the loss of opportunities that could positively affect your business, getting a better understanding of how to influence your soc 2 report and how to use soc 2 policy. We have dedicated support ready to. Browse our library of ebooks, policy templates, audit readiness checklists, evidence spreadsheets, and more free tools to simplify. Establish zero trust policies that align with soc 2 trust service criteria. We have dedicated support ready to. The system and organization controls (soc) 2 report, developed by the american institute of cpas (aicpa), has become a crucial standard for evaluating and demonstrating an. Review security policies and procedures. To avoid the loss of opportunities that could positively affect your. Save hundreds of hours and thousands of dollars on annual soc 2 compliance costs. Learn what a soc 2 policy template is and why you need them for your compliance project. Review security policies and procedures. Comply is free soc 2 compliance software for soc 2 certification. Track version history and changes to ensure continued. Policies must cover key areas like data protection, access controls, incident response, and employee responsibilities. We have dedicated support ready to. Edit and customize the policy to your organization’s needs; To avoid the loss of opportunities that could positively affect your business, getting a better understanding of how to influence your soc 2 report and how to use soc 2. Regularly review and update policies to keep them. Define roles and responsibilities for implementing and maintaining these policies. These policies are reviewed by the soc 2 auditor in great detail with respect to adherence to soc 2 controls and are expected to be documented and accepted by each. Edit and customize the policy to your organization’s needs; Our goal is. Learn what a soc 2 policy template is and why you need them for your compliance project. Regularly review and update policies to keep them. Comply is free soc 2 compliance software for soc 2 certification. Preparing for a soc 2 audit requires a thorough annual review of your security documentation and processes. The objective is to account for: These policies are reviewed by the soc 2 auditor in great detail with respect to adherence to soc 2 controls and are expected to be documented and accepted by each. We have dedicated support ready to. By providing businesses with a structured framework, soc 2 templates can save significant resources and time within the policy development stage. Review security policies and procedures. The system and organization controls (soc) 2 report, developed by the american institute of cpas (aicpa), has become a crucial standard for evaluating and demonstrating an. Policies must cover key areas like data protection, access controls, incident response, and employee responsibilities. Establish zero trust policies that align with soc 2 trust service criteria. Save hundreds of hours and thousands of dollars on annual soc 2 compliance costs. Edit and customize the policy to your organization’s needs; An access control policy defines how your organization manages user access to systems, data, and applications. Define roles and responsibilities for implementing and maintaining these policies.Soc 2 Policy Templates
Soc 2 Compliance Checklist Template
SOC 2 Information Security Policy Template Secureframe Secureframe
Soc 2 Compliance Checklist Template
25 SOC 2 Policy Templates to Prepare for SOC 2 Audit
25 SOC 2 Policy Templates to Prepare for SOC 2 Audit
GitHub gjyoung1974/soc2policytemplates Template SOC2 Policy
Soc 2 Compliance Checklist Template
Soc 2 Report Template
25 SOC 2 Policy Templates to Prepare for SOC 2 Audit
Soc 2 Policies Are A Comprehensive Set Of Guidelines And Procedures That A Company’s It Department Follows To Handle And Protect Customer Data.
To Avoid The Loss Of Opportunities That Could Positively Affect Your Business, Getting A Better Understanding Of How To Influence Your Soc 2 Report And How To Use Soc 2 Policy.
Track Version History And Changes To Ensure Continued.
Our Goal Is To Create Quality Templates So That Our Customers Can Avoid Rework And Focus On Their Actual Jobs Rather Than Doing Everything From Scratch.
Related Post: